Since December 2017, there have been hundreds of reports from around the globe (especially from UK, USA & Europe) about a possible mobile hack that takes control of victims’ mobile phones for mere financial and digital gain. This malicious attack has jeopardized the SIM carrier industry and stunned telecom users as none has been able to make systems hack-proof for such attacks.
However, to prevent ourselves, we need to dive deeper to find out its origin and learn about how this SIM-Jacking works.
What is SIM-Jacking?
Also called SIM-HiJacking, SIM-Jacking is a malicious trick, a way that hackers, fraudsters use by taking control over the mobile phone and hack bank accounts, crypto accounts and steal money from it.
Thieves exploit the mobile service providers’ security protocols to ‘port’ a phone number on a different or new SIM Card.
In other words, this is more like a techno-trick at first that later becomes a vital cybercrime. For instance, if a customer somehow breaks or loses his/her phone, then he/she can ask the mobile service provider to port the original phone number on a new SIM card and new mobile phone. To ensure if it’s really you, the providers may ask for your security information to legitimize the ‘port’ and after confirmation, ports the original phone number on a new SIM Card.
In August 2019, Jack Dorsey, CEO of Twitter, got his Twitter account hacked due to SIM swapping attack, and had nonsensical Tweets.

How does SIM-Jacking happen?
To carry out the hack, hackers need to have security information about the victim to port their victim’s phone number. Unfortunately, they can easily do that by:
- Sending ‘Text Messages’ with security information requests
- Phishing Email Scams
- Suborning an employee(s) of a mobile service provider
- Gaining your trust to know your personal information
- Data collected due to data breached in companies
These are the most possible ways a hacker sabotages the victim’s mobile phone and loots them in a matter of seconds.
Once they acquire the necessary security information of the victim, hackers then pretend to be as their victim and launch ‘port’ request to the mobile service provider. Once the number is ported on a new SIM card, the victim loses the network connection on mobile. All the calls and texts that were meant to reach him, will go to the hacker’s mobile.
Who are the Victims of SIM Swapping?
It is challenging at the moment to determine who the victims are but people from the UK, USA, and Europe have reported this incident. However, most of the victims are celebrities, politicians and notable figures.
Allison Nixon, Director of Research Flashpoint (security firm) had this to say on this rising SIM-Hack:
“I’ve been looking at the criminal underground for a long time, and SIM swapping bothers me more than anything I’ve seen. It requires no skill, and there is literally nothing the average person can do to stop it. “
“The customer service is trash. I couldn’t get no help” in a video said King Bach, an American-Canadian Actor, YouTuber, who was also strangled in the SIM-Swapping attempt when his phone number was hijacked in August 2019. After recovering the network, he responded heatedly in a video and blasted at AT&T for its ‘unhelpful service’.
“Second time My phone number was hacked because of human error within the company at @ATT?” said Amanda Cerny, American Actress. “time to switch carriers. Be careful out there everyone” she further added her network migration with grief-sigh. Likely, mobile carrier companies are clearly at fault, offering no stern measurements against SIM-Jacking.
The SIM-Hijackers hacked celebrities’ social media accounts to post offensive, bigotry comments.
Jessica Alba, a renowned American Actress, became the victim of SIM-Jacking in August 2019. However, no reports of SIM-Jacking were officially confirmed but the Tweets hackers posted from her account were similar to many other Tweets posted from other victim’s accounts. Chloe Moretz was also amongst the first celebrities to become the victim of SIM-Swop Hacking.
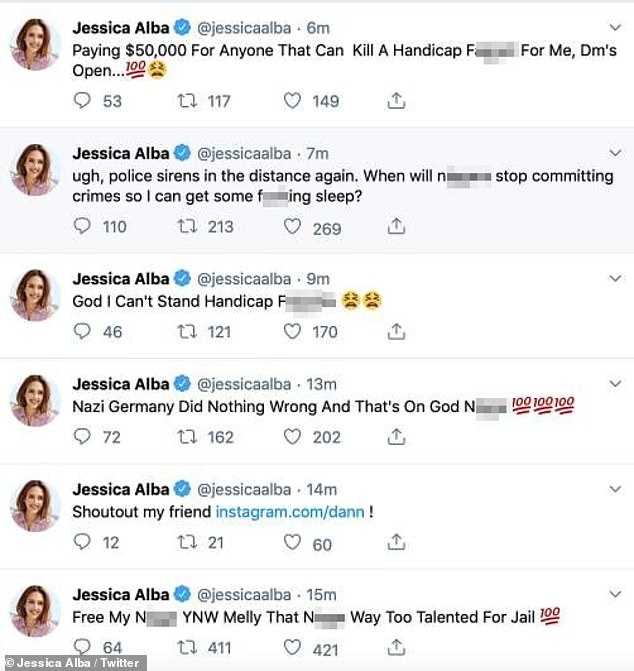
Shane Dawson, James Charles and Etika were amongst the Youtubers who got caught in the act. All the victims are holding the mobile service providers guilty as ‘insufficient measurements and lack of digital code’ prevailed.
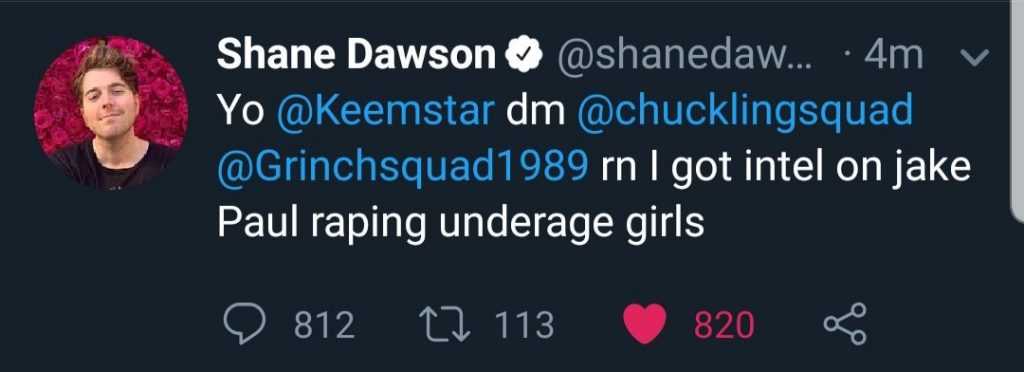
But is it just famous people?
On the 8th of January 2020, an individual, who wants to remain nameless in the course, approached Value Hosted and told us about his recent encounter with the SIM-Swop or SIM-Jacking. “My phone signals went offline, I was not getting text messages and my phone was showing a warning, cannot make phone calls through SIM,” said the victim. “they hacked one of my cryptocurrency accounts and stole about $300” he further added while speaking to our technical head.

“Such attacks only result in defamation and theft. But also, the mobile service providers should be held accountable for the breach” said Karim Rattani, Senior Technology Analyst who sat down with Noitcennok D. Director (Technical) at Value Hosted.
“I would blame the carriers for not having more robust ways to authenticate users,” said Mr. Joseph Hall, Cheif Technologist at the Centre for Democracy & Technology (CDT), Washington.
Similarly in Brazil, victims reported a similar hack that first hacked their WhatsApp and then sent messages of ‘urgent payment’ to friends & family on the list.
Mr. Robot for real? fsociety? Crypto-War?
Before coming with an entity to blame, a physical-level investigation should be conducted at carriers’ end as well as the victims. Elsa Ramon, a famous journalist/reporter, produced an extensive report on Cryptocurrency and a ‘possible link’ between SIM-Jacking.
“Crypto traders who store the Cryptocurrency for a long time at various online platforms and not transfer or use it for the value, are most likely to be singled out for SIM-Jacking” she further added. “the unfortunate part is no one can recover the Cryptocurrency or track the transaction” Ms. Ramon explained.
How can I prevent myself from SIM-Jacking hack?
- Contact your mobile service provider and ask them to double the security at your number
- Change your security information every 15-30 days
- Do not open (file, image, etc.) sent to you via email, text or social media
- Do not share your personal information with anyone no matter how close you are to that person
- Create strong, unique passwords for emails, bank accounts, Crypto accounts, online shopping, and social media
- Do not share personal details on social media
